5 True Stories That Prove You Shouldn't Piss Off The IT Guy

In a company full of people who don't understand computers, the IT guy is like a wizard. If you get a weird error message, you're not getting any work done until he makes it all better. In some offices, these guys wield more power than the owner of the company.
And if you want proof, just look at what happens when they get pissed off ...
Omar Ramos-Lopez Remotely Shuts Down 100 Cars

If we told you that a young computer whiz disabled more than 100 cars from his computer, you'd probably think "Man, this Hackers remake is gonna suck." That's the sort of wildly impossible feat that could only come from Hollywood's ridiculous conception of technology ("Oh no, the hackers have taken over our cars using their cache matrix nodes!") And yet, it happened. And here's the guy who did it:

Twenty-year-old Omar Ramos-Lopez was an employee for an Austin-based car dealership until February of 2010, when he was let go from the company and his passwords were revoked. His former coworker's passwords, however, were not. This was a problem for the customers of the Texas Auto Center.
You see, part of Ramos-Lopez's job involved using a system a called WebTeckPlus to remotely turn off the cars whose owners were late on payments -- basically, there's a little box installed inside every car that, upon receiving a wireless signal, can disable the ignition system. You can see where this is going.

Using someone else's password, Ramos-Lopez logged in to the system and shut down the cars of more than 100 random unsuspecting customers, who then proceeded to flood his former employer's office with angry calls since, you know, they weren't actually behind on their payments at all. Some of them even reported horns going off incessantly in the middle of the night, which was also within Ramos-Lopez's newfound powers and could only be stopped by going out and removing the car's battery. We're guessing that most of these people weren't even aware that something like this existed (we sure didn't) and assumed some sort of demonic possession was involved.
This caused a variety of problems. While the system can't shut down cars that are already in movement, anyone who was driving to work and stopped to buy a falafel suddenly found themselves stranded in the middle of the street. It took two days for Texas Auto Center to figure out what was causing this -- in the meantime, people missed work, missed school and had to spend money on tow trucks because of a jobless IT guy with too much time on his hands.

Employees at the dealership first noticed something weird was going on earlier the same month, when they were billed for $130,000 in GPS equipment no one remembered ordering. Also, Tupac Shakur had apparently purchased a 2009 vehicle from them, which would require either a time machine or enormous forethought on his part. Turns out Ramos-Lopez had been going over the company's database, changing names and messing with the records like a common Wikipedia vandal.
Eventually, the police tracked down Ramos-Lopez's IP address and charged him with breach of computer security and with being a dick. Which would be a terrible injustice if it turned out Ramos-Lopez was innocent and that Tupac's ghost was responsible for everything.

Walter Powell Turns a PowerPoint Presentation Into Porn

When Walter Powell, the former director of information management for the Baltimore Substance Abuse System, was fired from his job in 2009, he did not go quietly. And, where some of us might only leave a drunken message on the boss's voice mail, Powell used his computer expertise to remotely install password-stealing software on the company's computers. This gave him remote access to the work stations of several employees ... including his supervisor, BSAS CEO Greg Warren. Also known as the guy who fired him.
During the next month, Powell illegally accessed the BSAS network over 100 times and became their personal computer gremlin, "accidentally" forwarding confidential information to other people just for kicks, and sending out fake emails from the account of his former boss. We don't know what those emails said, but we can take a guess.

And then came his master stroke: Powell learned that Warren was set to deliver a PowerPoint presentation in front of the BSAS board of directors -- which, by the way, includes the mayor of Baltimore, the commissioner of the police department and the president of the Baltimore city council, among others.
At some point during the presentation, Powell hacked into Warren's computer, rebooted it and replaced a slide with a picture of a naked woman, which was displayed on the 64-inch screen.

"The clitoris represents our year-over-year revenue growth."
Powell's pranks ended up costing BSAS $80,000 in security upgrades. For all of his antics, he was only sentenced to 100 hours of community service and a two-year suspended sentence, but he received the distinction of being the first person to be charged by the city of Baltimore for computer hacking.

Terry Childs Holds San Francisco Hostage

In July 2008, the mayor of San Francisco walked into a jail with the specific mission of talking with one man imprisoned there: Terry Childs.
This prisoner held something of vital importance to the city: the passwords to a system that controls every network in San Francisco, which only he knew. Why did Childs have access to that system? Because he's the one who created it ... and the one who locked everyone out.

Childs had worked for the city as a computer engineer for about five years before he learned that he was about to get fired. So, he decided to take some insurance policies on his employment: He modified the networked system he had helped develop from the ground up, which controls everything from the mayor's email account to police records to inmate bookings, and changed it so that only he could access it.
When his employers asked him for the codes, he refused to give them up and was arrested. Even in jail, he would only give out fake codes, presumably just to mess with everyone since he was obviously beyond fired at this point.

Officials could still access the network, but they couldn't modify it on an administrative level, since Childs was the only administrator. The city set a bail of $5 million (five times more than a murder defendant) because they feared that if Childs got hold of a computer, he would log in to the network and delete everything -- the mayor later admitted that San Francisco was "in peril" because they were locked out of the network. The city spent nearly $1.5 million desperately trying to regain access (and failing) and testing further vulnerabilities that could potentially make them look stupid.
Childs, who was sentenced to four years in prison and charged a $1.5 million fine, was so paranoid that when he first learned about his possible firing he created a tracing system that would let him know what his coworkers were saying about him.

After 12 days of sitting in a jail cell, Childs finally agreed to give out the passwords ... but only if the mayor himself came to play Clarice Starling with him, saying he didn't trust other people with the passwords to "his" creation. We're surprised he didn't send the mayor all around the city solving clues to piece the password together like the goddamned Riddler.
Joseph Nolan and Jason Cornish Should Not Be Trusted With Passwords

Not every hacker out there is a computer genius: Sometimes all it takes to do some serious damage is a little password. It seems really obvious, but one thing that security experts have to keep reminding companies is that if you're gonna fire someone, it might be a good idea to change your damned passwords. Especially if the guy you fired happened to be a vindictive asshole.
Take Jason Cornish, a former IT administrator at the U.S. subsidiary of Japanese drug company Shionogi, who, after being fired for the second time that year (he was let go in July 2010 but brought back as a consultant, then fired again in September), decided to spend his wealth of free time messing with his former employer.

Over the next four months, Cornish attempted again and again to access the company's network -- using the passwords and system knowledge he acquired while working there -- until he succeeded in February 2011 and trashed 15 virtual hosts containing vital information. Oh, and he did that while sitting in a McDonald's, leeching off their free Wi-Fi.
Cornish's attack "froze Shionogi's operations for a number of days" -- employees were no longer able to ship products, cut checks or send emails, because all that stuff and more depended on the hosts that he deleted. Perhaps he wanted his former colleagues to know what it feels like to be unemployed and have nothing to do all day, although it's more likely that he was just being a douche. His attack cost Shionogi $800,000 in damages, and Cornish now faces 10 years in jail and a hefty fine. It wasn't hard to catch him; while he was smart enough to do it from the McDonald's public Wi-Fi connection instead of his own, he actually used his fucking credit card to buy food there five minutes before the attack.

But Cornish isn't the only disgruntled IT guy of dubious intelligence who abused passwords to get revenge on his old company. Joseph Patrick Nolan resigned from the Ann Arbor-based Pentastar Aviation in January 2007, but later found out that he wouldn't get his last paycheck because he neglected to sign his separation agreement in time. Nolan took the news like the mature 26-year-old that he was, by which we mean that he logged in to the company's computer system and took a shit all over it.
Nolan accessed his former employer's database and proceeded to obliterate an entire computer drive containing personnel information and payroll records, presumably figuring that if he didn't get paid, no one else should. It cost the company between $30,000 and $50,000 to repair the damage over the next few months, and in the meantime everyone at the office had to be called "that guy" or "that other guy."

At least Cornish carried out his anonymous attack from a public Wi-Fi connection -- Nolan did it from his own apartment, and it's not clear how anyone mildly familiar with computers could have expected to get away with it. He was sentenced to four years probation, had to pay $1,158.25 to Pentastar and was even shamed into quitting his sweet new job as a senior infrastructure specialist at the Ann Arbor Information Technology Department. Hopefully he remembered to sign the damn agreement this time.
Timothy Lloyd Plants $10 Million Time Bomb

When Timothy Lloyd was fired from Omega Engineering, a company that produced equipment for the U.S. Navy and NASA, his employers thought they'd finally gotten rid of a rogue programmer who bottlenecked and sabotaged projects to make his colleagues look bad and generally acted like a massive dick toward everyone. He was like every bad IT guy stereotype put together. What they didn't know was that even after he was gone, Lloyd would continue haunting them through six little lines of code he had written into the main computer that would pretty much ruin the entire company:
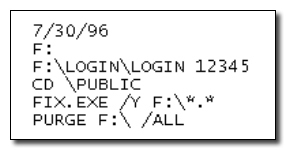
We're assuming every programmer reading this just shat their pants.
Lloyd had worked at Omega since the '80s and was at one time their star employee. However, as Omega expanded, Lloyd felt he was losing relevance and being marginalized (his being a dick probably didn't help). Rather than stepping up his game and proving he still had it, Lloyd started devising a Machiavellian plan. In early 1996, months before his firing, he began testing a little program that would be triggered at a specific date, running a simple line of code that would delete a certain sector of the main server.
At the same time he started centralizing the most important documents in the company's file system in the same place, and asked for access to the only backup tapes for those files. Meanwhile, he began visiting job fairs and interviewing at other companies.

And so on July 10, 1996, Lloyd had to act all surprised when he was finally fired from Omega, doing his best to suppress the maniacal laughter roaring inside of him. Because, you see, exactly 20 days after his firing, on July 30, employees at an Omega manufacturing plant in New Jersey logged in to a computer terminal ... and everything was deleted. More than a thousand design and production programs (i.e., the whole thing they did at Omega) were wiped out in seconds, which ended up costing a staggering $10 million to the company and killing their bright future. In the '90s Omega was a rising manufacturer with contracts all over the world -- today they don't even have their own Wikipedia page, and it's probably all on this guy.
But wait, how could something like that even happen? Didn't they have backups or something for such important files? Yep -- Lloyd had taken them home in the weeks before his firing (along with $50,000 worth of stolen equipment) and deleted them. The baffling thing here is that Lloyd created this complex plan to get revenge on something that hadn't happened yet -- he knew he was such a colossal dick that they had to fire him at some point, and in preparing for the eventuality gave them an even better reason to do it.

He was eventually sentenced to three years in prison and ordered to pay a $2 million restitution. While his career as a programmer is probably dead by now, we think he could make some decent money doing consulting work for supervillains.
Benjamin Buso lives in Texas and is currently seeking employment in security consulting.
For more insight into people you should be careful around, check out Why Tech Support Sucks: A Look Behind the Scenes and 6 Reasons The Guy Who's Fixing Your Computer Hates You.
And don't forget to follow us on Facebook and Twitter to get sexy, sexy jokes sent straight to your news feed.
What the Hell Did I Just Read: A Novel of Cosmic Horror, the third book in David Wong's John Dies at the End series, is available now!
